

Modernising a legacy system isn’t about replacing everything at once.
It’s about controlling how requests flow while the old and new systems run side by side.
The Strangler Fig pattern gives teams a safe path to do this.
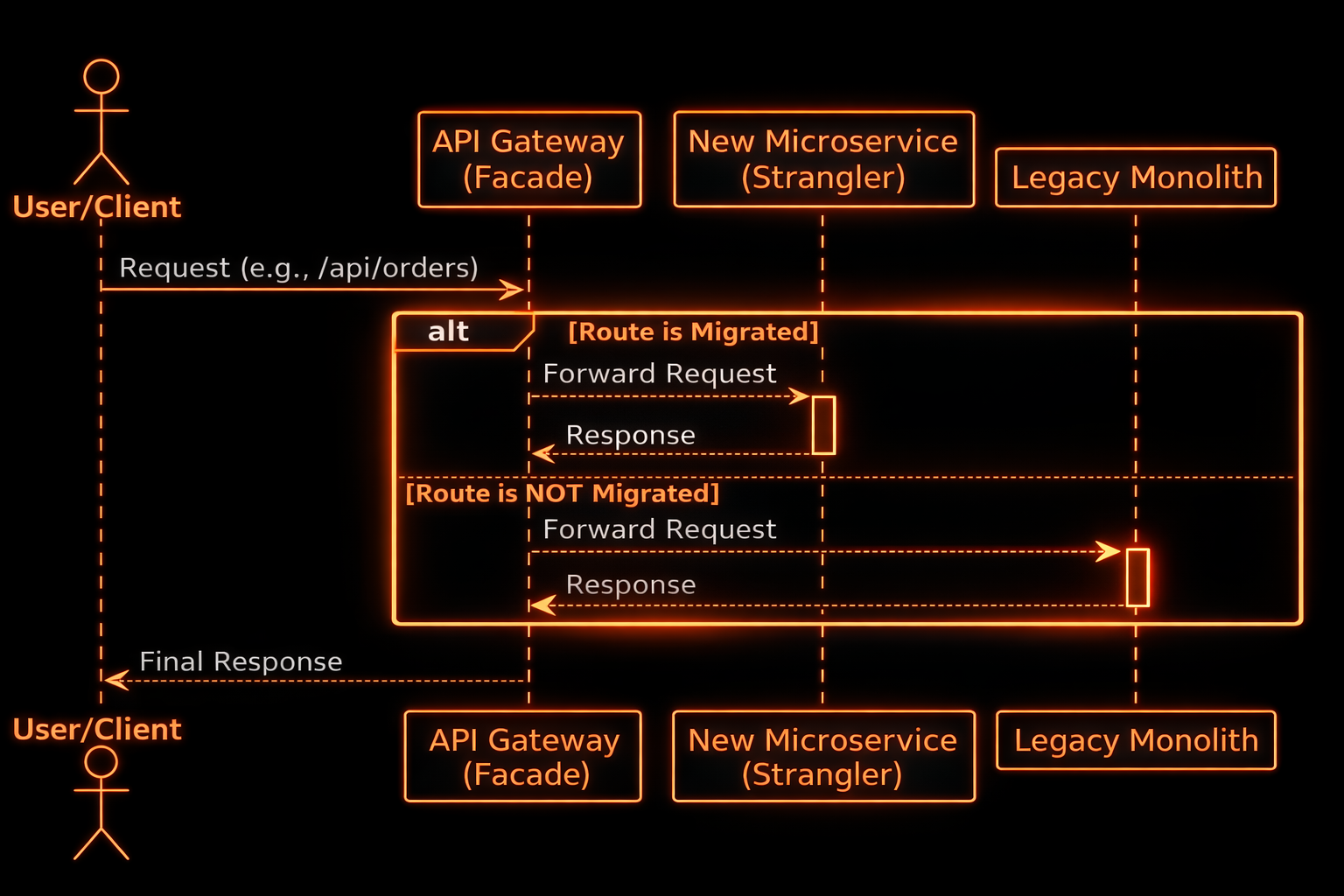
But the real enabler isn’t the new services, it’s the API façade that decides, on every request, whether traffic goes to the monolith or the new module.
This article breaks down how that façade works, why it matters, and the practical patterns that make stepwise modernisation predictable.
The Strangler Fig pattern only works when you can do two things reliably:
An API gateway gives you both.
Think of it as the single entry point that gradually swaps the old for the new, without forcing an overnight cutover.
The API gateway becomes the operational control centre.
Without it, the migration becomes unpredictable and risky.
These map directly to the pain points we see in legacy modernisation projects across clients:
The gateway doesn’t replace the monolith.
It simply controls the environment around it, and that’s what makes modernisation realistic.
All traffic goes directly to the monolith:
Client → Monolith → Database

It’s functional, but rigid. Every change carries system-wide risk.
Traffic now flows through a controlled, observable entry point:
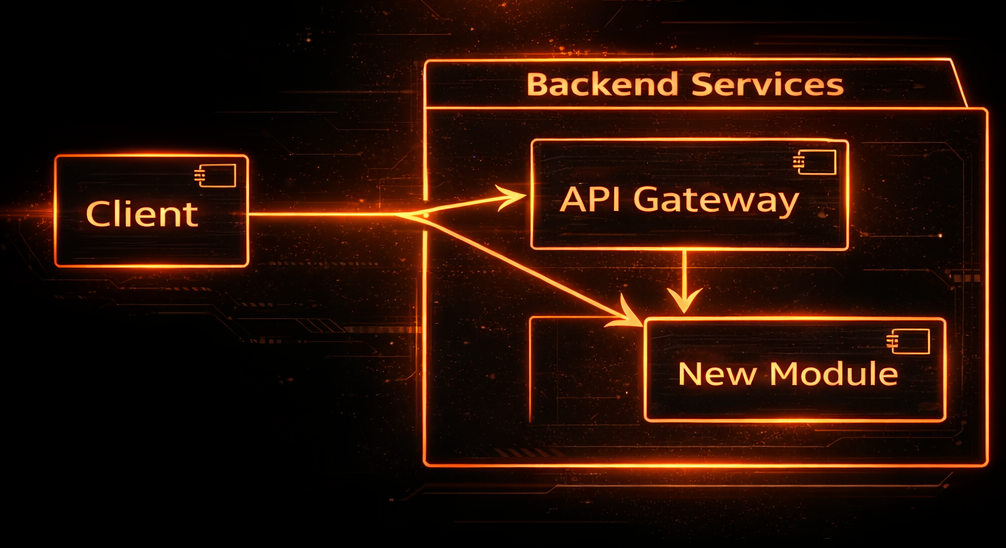
The gateway becomes the single entry point.
Now you can begin peeling away domains safely:
/auth → new service/invoices → migrate gradually/orders → keep in monolith temporarilyThis is how teams modernise without an overnight switch.
The façade doesn’t just route traffic — it decouples the migration timeline from the release timeline.
Teams can deploy new modules without exposing them to users immediately.
Feature flags allow:
Flags become a non-negotiable tool for rolling out new capabilities safely.
A gateway allows routing by percentage, geography, cohort, or authentication level.
This achieves something a monolith could never do:
validate new services under production load without risking everything.
Example flow:
Zero downtime. Zero drama.
A common failure mode: the gateway becomes too smart and absorbs business logic.
To avoid this:
The façade should coordinate traffic — not run the business.
Most modernisation projects live in this temporary state for months or years.
A healthy mid-flight architecture has:
This ensures progress does not compromise reliability — a key principle in our work at Itsavirus.
A practical sequence we use in real migration projects:
Mirror traffic, add observability, keep all requests flowing to the monolith.
Example: /search, /auth, /notifications.
Start with low volume, validate, expand.
This iterative rhythm is what makes the Strangler Fig pattern predictable and safe.
Most organisations we work with cannot afford unpredictable migrations.
The façade gives them:
It offers clarity, safety, and operational control — the same principles we emphasise across our AI and modernisation projects. itsavirus_context_profile
The Strangler Fig pattern is not just a conceptual model.
It is an operating model that relies on a robust, disciplined façade to make modernisation feasible.
With the right gateway strategy:
If you're planning to modernise a legacy system, or want to validate whether your gateway strategy is sound, feel free to reach out to our representative here.
We’re always open to share insights or walk through real examples from our work.




